Effective cybersecurity hinges on strategic identity management.
The top providers of modern cyber security must integrate advanced identity practices into every facet of the organization’s defense strategy. Industry compliance and concerns are at the forefront of CISOs’ minds when addressing the top concerns a modern business faces. These concerns circle around eight CISO Priorities that are identified as beneficiaries or contributors to a healthy Identity and Access Management program.
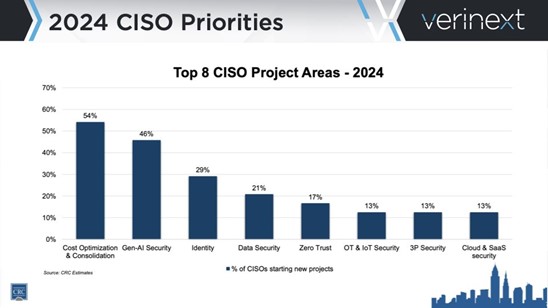
Identity protection is found at the center of lifecycle management, access management and privilege access management. It is essential to unpack the impact and importance of these eight core CISO concerns.
- Cost Optimization and Consolidation: To streamline operations without compromising security consider efficient resource allocation and integrated security solutions. Seek identity-driven cost optimization to ensure that security investments are aligned with business needs, maximizing ROI while minimizing risks.
- Gen-AI Security: Harnessing AI’s potential while safeguarding against AI-driven threats, ensuring robust defenses in the era of machine learning is a highly discussed concern. Focus on selecting identity-centric AI security solutions to enhance threat detection and response capabilities, leveraging behavioral analytics and identity context.
- Identity: Identity management is pivotal, securing access through strong authentication and authorization mechanisms. By strengthening identity governance, you can ensure that only authorized personnel and systems access critical resources, mitigating insider threats and unauthorized access.
- Data Security: Data security continues to be top of mind for every enterprise. Protect your data with encryption and comprehensive data handling practices to maintain confidentiality and integrity. Identity-based data security measures ensure that sensitive information is accessed only by authorized users, preventing data breaches and ensuring compliance with data protection regulations.
- Zero Trust: With Zero Trust, users can verify every request, enhancing security posture by minimizing trust assumptions across all transactions. Identity-driven Zero Trust frameworks enforce strict access controls based on user identity and behavior, mitigating lateral movement and reducing attack surfaces.
- OT & IoT Security: It is important to secure operational and IoT devices to mitigate vulnerabilities in interconnected environments. Identity-driven access controls and device authentication protocols safeguard IoT and OT assets, preventing unauthorized access and potential disruptions.
- Third-Party Security: Enterprises need to strengthen vendor partnerships through rigorous security assessments and contractual obligations. Identity-centric third-party risk management ensures that vendors adhere to security standards and access controls. Reducing supply chain vulnerabilities is the gold standard.
- Cloud & SaaS Security: Lastly, safeguard cloud infrastructure and SaaS applications with stringent security controls and monitoring. Identity-based cloud security policies enforce granular access controls and multi-factor authentication, protecting data in cloud environments from unauthorized access and data breaches.
To unlock exceptional modern cybersecurity framing, use these eight CISO pillars as your guide.
At Verinext, we’re pioneering a new era of security excellence by integrating advanced identity practices into every facet of our customers’ defense strategies, protecting them from today’s threats and whatever comes next. To learn more about our options, view this security solution webpage and give us a call!
Related Posts:
DR Journal: Preparing for the Worst: How DRaaS Can Save Your Business
3 Steps to Use Data Classification to Elevate Your Security Posture