Automating Security at the Endpoint
Sophisticated cyberattacks which target the endpoint continue to be a major threat, and a significant risk. Ponemon reports that 68% of IT and security professionals said the frequency of cyberattacks [...]
Strategy & Factory Pattern in Spring Boot Application: Part II
Strategy and Factory patterns are the most useful design patterns in any application. If you have a branching code with lots of ‘if and else’, then Strategy pattern is the [...]
Strategy & Factory Patterns in Spring Boot Application: Part I
Strategy and Factory patterns are the most useful design patterns in any application. If you have a branching code with lots of ‘if and else’, then the Strategy pattern is [...]
5 Ways to Reduce Network Costs
As companies strive to control costs, networking teams must be ready to respond to calls for reductions. Unfortunately, network costs are traditionally considered tough to trim. After all, expensive single-manufacturer [...]
Migrating a VMware MS SQL Cluster with RDM Disks
When migrating your VMware environment to a new SAN or storage provider, edge cases often require special attention. One such case involves virtual machines with Raw Device Mapped (RDM) LUNs. [...]
Risk Assessment Can Protect Your Data and Business
Your business data is threatened by many types of risk – everything from natural disasters, data center outages, breaches by hackers, and even disgruntled employees. Mitigating the risk of data [...]
7 Key Tools for Network Security Teams Battling Cyber Threats
(and they don’t get in the way of business either) The elevated levels of cyber threat activity that now occur on a daily basis are leading most network security teams [...]
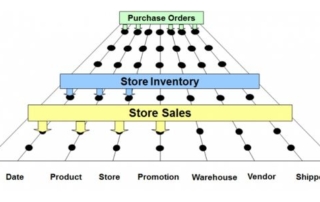
The Power of the Bus Matrix
When starting a data warehouse or business Intelligence effort, we go through a step-by-step process to get the information necessary to design and construct the pieces to satisfy the effort. [...]