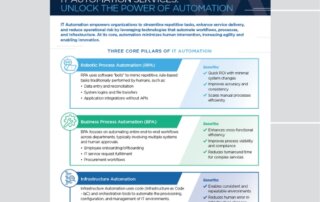
SmartOps Monitor Solution Brief
Verinext’s Event Intelligence-as-a-Service (EIaaS) solution, SmartOps Monitor, is your shortcut to real, measurable outcomes — not just more dashboards. We combine the power of enterprise-grade event intelligence platforms with our [...]