Infrastructure Security
It will not have escaped anyone’s attention that certain applications have come under scrutiny for being buggy, leaky, or maybe simply downright undesirable to a corporation or government entity. Here we’ll look at a scenario where devices can be prevented from connecting to Microsoft 365 services when Intune detects that such apps are present on the device.
Compliance
Taking a look at device compliance first. Devices that are enrolled in Intune can be marked as Compliant or Not Compliant. There are many ways to make a device non-compliant, but in this case having Intune check for a particular application is one way. If Intune detects an application the process will make the device non-compliant and trigger a refusal of access to corporate assets. How then, to make that happen?
Blocking the Application
In order to block an application through the compliance route there must of course be a compliance policy. Let’s go with the current nemesis of politicians worldwide and look at TikTok. The first thing you need is the app ID and that’s easily enough found by using Intune to start adding the app. Search the app store and you’ll get the app ID as shown below at the end of the URL.
Figure 1: App Store ID

You can see the app ID in the browser. Take that number and in another window enter https://itunes.apple.com/lookup?id=835599320. Note that the URL is not the same as the link from the app store. The important part is the app ID here. For any other app that you wish to ban the link is the same apart, of course, from the app ID.
You will then get sent a txt file and in that file is the bundleid. Search for that word and you will find that there’s only one instance. In this case, it’s com.zhiliaoapp.musically.
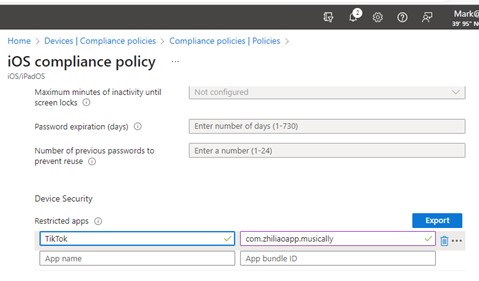
Go to the Intune admin center and create a new compliance policy for iOS. Drill down to System Security and then to Restricted apps. Enter the previously noted details as below.
Figure 2: Intune Policy
Carry on through the rest of the wizard and select the assignment to All Users, or a pilot group to test, and then complete the policy.
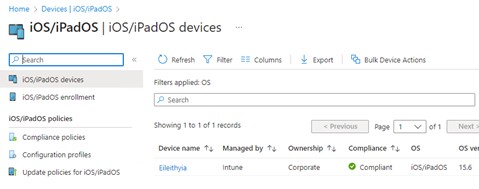
Look at the compliance state of the iOS devices. In this example, there is only one test device and it is marked as compliant.
Figure 3: Device Compliance (1)
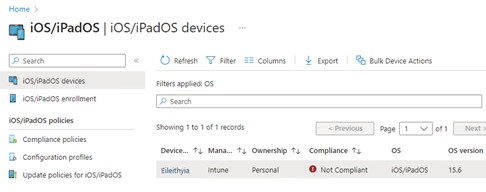
After a short period of time the compliance state will change to Not Compliant.
Figure 4: Device Compliance (2)
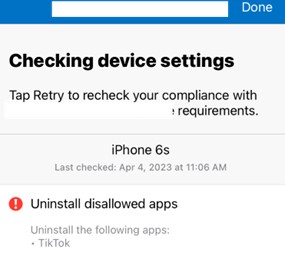
The end user will receive a notification that their device is out of compliance if you set that as part of the policy. Their Company Portal app will display the notification as well, telling them to remove the app.
Figure 5: Device Notification
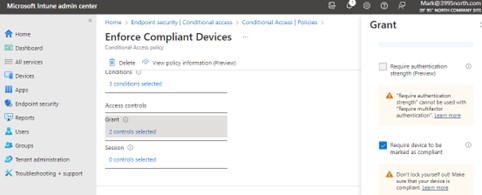
This will trigger the Conditional Access policy that you have previously set up to deny access to resources. There are a great many options in terms of selecting what apps may be accessed and from what locations, but the basic takeaway is that you can set the CA policy to require compliant devices and then set a compliance policy to restrict apps.
Figure 6: Conditional Access Policy
Summary
It is difficult to have users follow instructions on what they can and cannot download and use, but it is perfectly possible to protect your corporate data from any applications that users have chosen to download to their iOS devices.
These quick steps will permit you to take the app referenced here and any others that are deemed undesirable at the corporate level off devices or make those devices unable to access corporate data. The end users then have a choice; whether to remove the application to access data or use a different device that does not contain the restricted apps.
Learn more on how Verinext can support your customer experience and end-users, or contact us today.






