Introduction
As is normal with such things there are multiple guides to implement various technical solutions and often confusion can arise on what guide is right for you and which set of steps should be followed. This is part one of a two-part set showing firstly how to implement DUO on Microsoft 365, followed by a second guide to set up DUO on-premises so that application servers and even Microsoft servers can be made subject to DUO when using RDP to gain access to them.
Configure DUO
Step one in the process is to get the configuration file from DUO that you need to enter into Microsoft 365. Go to your DUO administration console and select Applications and then Protect an Application. Search for Microsoft. Select the Microsoft Azure Active Directory option. If you are protecting others such as Microsoft RDP (next article) you will find this on the list as well. If you, as the Microsoft 365 administrator do not have access to the DUO administration console you can work with the DUO administrator to get the information you need. Either the main DUO administrator needs to give you access or you need to give the DUO administrator brief access so that they can run the authorization process that follows here.
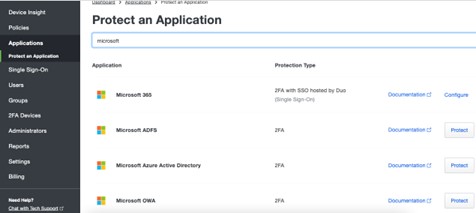
Selecting the option to protect will bring up the usual authorization screens so that DUO can get your tenant ID and other details. The person doing this will briefly need Global Administrator permissions in the Microsoft 365 tenant.
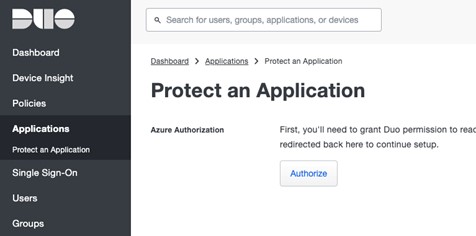
Doing this will generate a script as shown below. This is what you will copy and enter into Microsoft 365.
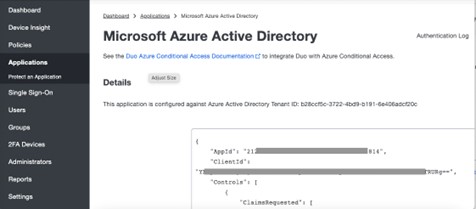
Configure Microsoft 365
Copy the text and move to your Microsoft 365 tenant, navigating through to Endpoint Manager and then Conditional Access.
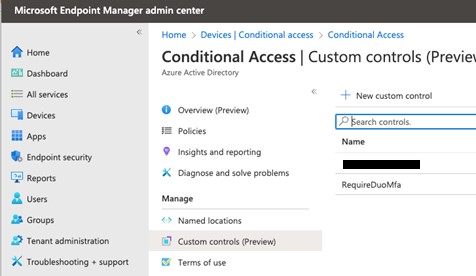
Go to Custom controls and add a new one.
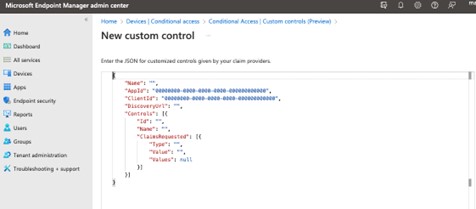
Replace the default JSON text as shown above with the data copied from DUO and save it.
Next go to the Conditional Access policies and create a new one. In the screenshot below there are already some created, and I won’t go into the minutiae of creating the policy except to show where you’re adding the custom control bears fruit.
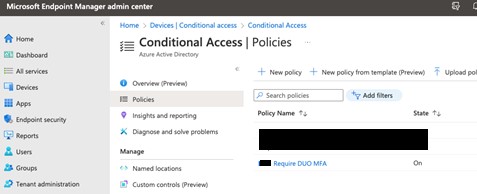
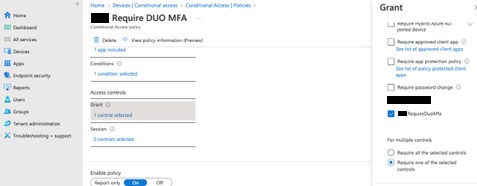
In the Conditional Access policy, go to the Grant section and you will see a new tickbox that matches the name in the custom control that you just created. Tick that box.
In the user assignments section enter either individual users or a security group so that you can manage who is and who is not sent out to DUO to provide that second authentication factor.
Obviously, in addition, there’s nothing to stop you from selecting other conditions such as not requiring DUO MFA if the users are in a trusted location or are accessing some other application. All the usual Conditional Access information is available to you.
Configure Additional DUO Settings
Whilst this article is not the place to go through the whole setup process for DUO such as directory synchronization, there are some settings that might need adjustment.
We recently came across a situation where some users wanted to have the MFA code read to them on their desk phones. This is not in the default policy.
At the bottom of the Application > Microsoft Azure Active Directory screen (shown above) is the option to Edit Global Policy. The “Phone Callback” option can be selected. When users enroll they can enter that phone number and then when the user attempts to access a protected service, their phone will ring, and the system will read out six numbers.
Summary
This is intended as a quick guide to allow the Microsoft 365 administrator to understand the handful of steps that need to be taken in both the Microsoft 365 and DUO admin consoles to introduce DUO MFA to the end users and configure the Conditional Access policies to implement it. Obviously, the person handling the DUO setup will have done the initial configuration and the synchronization from either on-premises AD or Azure AD. Users will have previously been instructed to set up their DUO profiles on their Smartphones or other devices.
Verinext can assist you with Microsoft 365 and DUO setup from start to finish. Contact us today.






